When multiple WAEs exist in a service group, WCCPv2 automatically distributes redirected traffic across all WAEs in the service group. When traffic passes through an IOS device with WCCPv2 redirection configured, the IOS device assigns traffic for that connection to a bucket. Read more…
The routers and WAEs participating in the same service constitute a service group. A service group defines a set of characteristics about what types of traffic should be intercepted, as well as how the intercepted traffic should be handled. There are two types of service groups:
- Well-known services
- Dynamic services
Well-known services, also referred to as static services, have a fixed set of characteristics that are known by both IOS and WCCPv2 client devices. Read more…
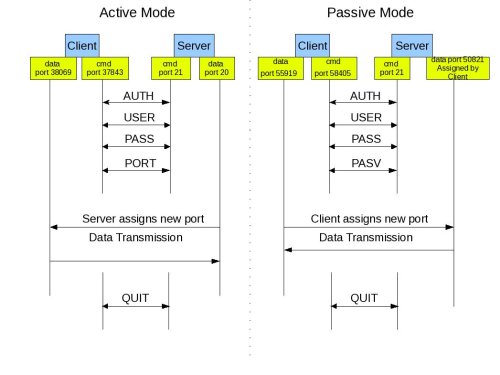
Active FTP:
In active mode FTP the client connects from a random unprivileged port (N > 1023) to the FTP server’s command port, port 21. Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server. The server will then connect back to the client’s specified data port from its local data port, which is port 20.
From the server-side firewall’s standpoint, to support active mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s port 20 to ports > 1023 (Server initiates data connection to client’s data port)
* FTP server’s port 20 from ports > 1023 (Client sends ACKs to server’s data port)
Passive FTP:
In order to resolve the issue of the server initiating the connection to the client a different method for FTP connections was developed. This was known as passive mode, or PASV, after the command used by the client to tell the server it is in passive mode.
In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server. When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1023 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command. The result of this is that the server then opens a random unprivileged port (P > 1023) and sends the PORT P command back to the client. The client then initiates the connection from port N+1 to port P on the server to transfer data.
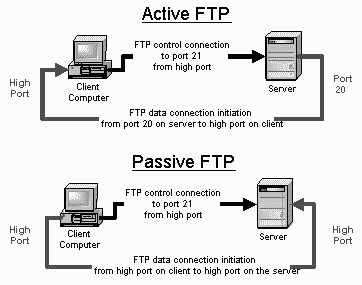
From the server-side firewall’s standpoint, to support passive mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s ports > 1023 from anywhere (Client initiates data connection to random port specified by server)
* FTP server’s ports > 1023 to remote ports > 1023 (Server sends ACKs (and data) to client’s data port)
This PDF describes the deployment strategy in detail, including planning, deployment and lessons learned. A very useful document if you are planning a large VoIP upgrade or installation. VIEW PDF
How to set up an IPSec tunnel between two LANs using the same subnet.
Conflicting LAN IP subnets can cause difficulties when routing through a tunnel. This configuration uses NAT to overcome the problem of duplicate addresses: Read more…
Planning for Voice over IP requires an understanding of the various headers added when transporting packetised voice, espcially over an IPSec VPN: Read more…
Deciding upon a QoS Classification and Marking strategy can be a difficult task. Cisco have provided certain recommendations which may be implemented as a baseline QoS strategy and then altered over time: Read more…
The basic QoS Model
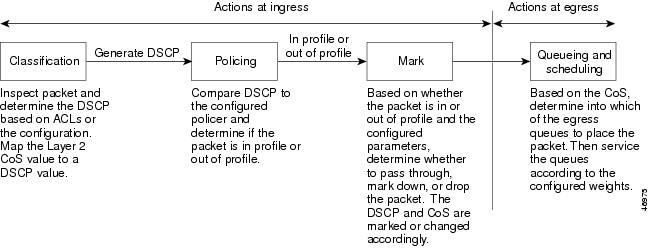
Actions at the ingress interface include classifying traffic, policing, and marking: Read more…
RFC 4594 describes some example and provides guidelines for DiffServ service classification which may be used as guidelines or as a basis for a QoS Classification Strategy: Read more…
The Modular QoS CLI (MQC) command structure found in Cisco IOS® Software requires a class map is built incorporating the ACLs that identify the traffic that will have QoS applied to them. Read more…



