There may be an occasion to setup a site-to-site VPN with a customer or partner network but due to the risk of overlapping private RFC1918 address space, to use a single public address and Port Address Translation. This methos uses a single IP address in a NAT (PAT) object. This example uses simplified NAT available from ASA software version 8.3+
crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
ccrypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac Read more…
This script is a simple, interactive way to backup and date-stamp your juniper Netscreen ISG/SSG (ScreenOS) firewall configurations. The script copies the configurations from the firewall using scp. Configurations older than one day ( -mtime +1) are archived off to a bz2 compressed file. Archives older than 60 days ( -mtime +60 ) are removed from the disk.
The usage is: nsb.sh [ip address / hostname of Netscreen]. (VIEW SCRIPT)
Read more…
The steps to create the (Windows) .msi are as follows:
STEP 1: Download the ISO file from cisco.com software download navigator page (http://software.cisco.com/download/navigator.html ) Read more…
This aide-memoir describes and compares NAT configuration (Identity NAT, NAT Exemption/Identity NAT and also compares the syntax between ASA version 8.4.2 and below. There are some considerable differences to the syntax and some of the better-known commands have been deprecated. Read more…
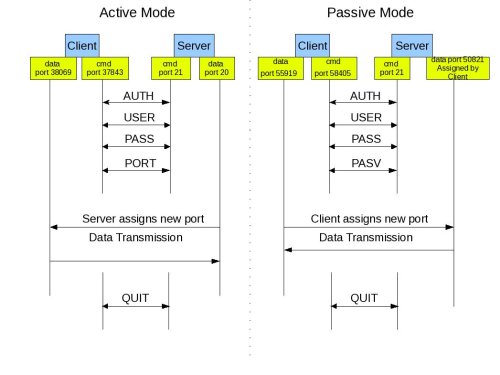
Active FTP:
In active mode FTP the client connects from a random unprivileged port (N > 1023) to the FTP server’s command port, port 21. Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server. The server will then connect back to the client’s specified data port from its local data port, which is port 20.
From the server-side firewall’s standpoint, to support active mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s port 20 to ports > 1023 (Server initiates data connection to client’s data port)
* FTP server’s port 20 from ports > 1023 (Client sends ACKs to server’s data port)
Passive FTP:
In order to resolve the issue of the server initiating the connection to the client a different method for FTP connections was developed. This was known as passive mode, or PASV, after the command used by the client to tell the server it is in passive mode.
In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server. When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1023 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command. The result of this is that the server then opens a random unprivileged port (P > 1023) and sends the PORT P command back to the client. The client then initiates the connection from port N+1 to port P on the server to transfer data.
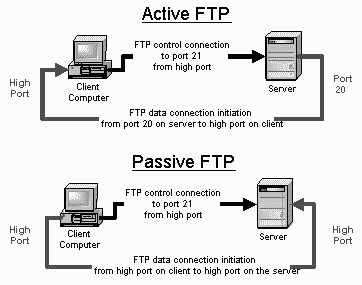
From the server-side firewall’s standpoint, to support passive mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s ports > 1023 from anywhere (Client initiates data connection to random port specified by server)
* FTP server’s ports > 1023 to remote ports > 1023 (Server sends ACKs (and data) to client’s data port)
TCP and UDP small servers are servers (daemons, in Unix parlance) that run in the router which are useful for diagnostics. Read more…
Here is a basic PIX configuration, which achieves the following:
– NAT overload from an inside network to an outside network
– Accept incoming PPTP VPN connections from ouside clients
– Turns on the web-based GUI on the PIX Read more…


