Understanding Traffic Shaping
Traffic Shaping involves in queueing traffic rather than dropping it. Traffic Shaping terminology is: Read more…
Traffic Shaping involves in queueing traffic rather than dropping it. Traffic Shaping terminology is: Read more…
Concurrent writes to a single file are not desirable in any operating system. To prevent this, most operating systems use locks to guarantee that only one process can write to a file at a time. Operating systems traditionally lock entire files, although newer ones allow a range of bytes within a file to be locked. If another process attempts to write to a file (or section of one) that is already locked, it will receive an error from the operating system and will wait until the lock is released. Read more…
This table compares QoS values for IP precedence, Differentiated Services Code Point (DSCP) and Multiprotocol Label Switching (MPLS) Experimental (EXP) values along with standard values used in Cisco IOS Software for configuration. Read more…
To understand how to interpret the show policy-map interface command, you first need to understand the concept of congestion.Conceptually, congestion is defined by the Cisco IOS software configuration guide as: “During periods of transmit congestion at the outgoing interface, packets arrive faster than the interface can send them.” Read more…
In order to authenticate against Kerberos realms and perform remote administration, the system must have the krb5-workstation package installed. Read more…
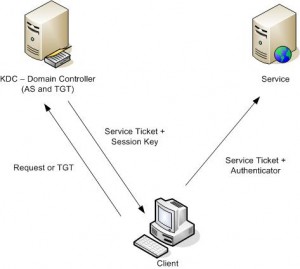 The Kerberos authentication method originated at the Massachusetts Institute of Technology in the 1980s.
The Kerberos authentication method originated at the Massachusetts Institute of Technology in the 1980s.
It was part of a project called Athena that involved integrating the computers on the MIT campus, which ran on different operating systems, in a network that offered single sign-on (SSO).
At that time, most UNIX systems allowed users to access their resources as long as they had an account name and password. Read more…
An aide-memoir. This example uses dual distribution layer switches for load-balancing VLAN traffic using MST: Read more…