ngrep is a “network grep” utility that can be used to match regular expressions within network packet payloads. This is a very handy utility as many network analysers (“packet sniffers”) can examine the packet header, but either do not display or cannot filter based on packet payload. Read more…
Active FTP:
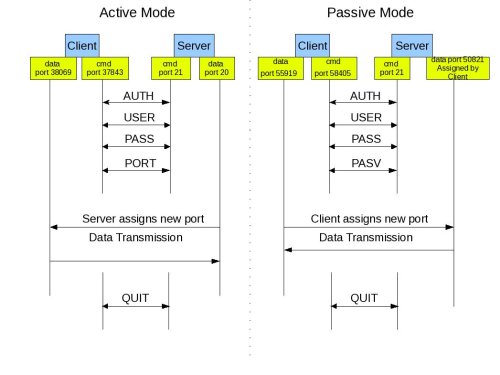
In active mode FTP the client connects from a random unprivileged port (N > 1023) to the FTP server’s command port, port 21. Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server. The server will then connect back to the client’s specified data port from its local data port, which is port 20.
From the server-side firewall’s standpoint, to support active mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s port 20 to ports > 1023 (Server initiates data connection to client’s data port)
* FTP server’s port 20 from ports > 1023 (Client sends ACKs to server’s data port)
Passive FTP:
In order to resolve the issue of the server initiating the connection to the client a different method for FTP connections was developed. This was known as passive mode, or PASV, after the command used by the client to tell the server it is in passive mode.
In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server. When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1023 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command. The result of this is that the server then opens a random unprivileged port (P > 1023) and sends the PORT P command back to the client. The client then initiates the connection from port N+1 to port P on the server to transfer data.
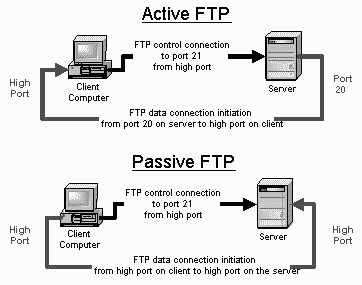
From the server-side firewall’s standpoint, to support passive mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s ports > 1023 from anywhere (Client initiates data connection to random port specified by server)
* FTP server’s ports > 1023 to remote ports > 1023 (Server sends ACKs (and data) to client’s data port)
Introduction
Riverbed Steelhead as WAN accelerator is deployed in WAN environment when traffic between WAN network (i.e. MPLS, Frame Relay) need to be optimized, hence creating so-called “WAN acceleration”. With “standard” WAN network consists of WAN routers and LAN switches, typically the Riverbed Steelhead is in place inline between the WAN routers and LAN switches. The f9llowing is an illustration: Read more…
Copy this text into a file with a “.reg” extension, then double click to update registry (caution: backup registry beforehand)
[HKEY_CLASSES_ROOT\telnet\shell\open\command]
@=”putty.exe %1″
The Image Verification feature, added in Cisco IOS Software Releases 12.3(4)T, 12.0(26)S, and 12.2(18)S, builds on the MD5 File Validation functionality to more easily allow network administrators to verify the integrity of an image file that is loaded on the Cisco IOS file system of a device. Read more…


