Secure Hashing Algorithms SHA-1 and SHA-2
First implemented by the National Security Agency (NSA) in 1993, the Secure Hashing Algorithm (SHA) is used by certification authorities such as Verisign and Thawte to sign certificates and Certificate Revocation Lists. SHA is used to generate unique hash values from files.
This is the SHA-1 hash fingerprint from the bbc.co.uk website:
root@raspberrypi:/# echo | openssl s_client -connect bbc.co.uk:443 2>/dev/null | openssl x509 -fingerprint -noout
SHA1 Fingerprint=EA:D2:F2:79:18:A0:CD:2B:10:3B:12:01:CF:B1:9E:CC:AF:0F:28:0C
SHA versions:
- SHA0 Obsoleted
- SHA1 Currently the most widely implemented
- SHA2 Stronger than SHA-1 due to longer hash (SHA224, SHA256, SHA384 and SHA512)
As part of their SHA-2 migration plan, Microsoft, Google, and Mozilla have announced that they will stop trusting SHA-1 certificates. Google began phasing out trust in SHA-1 certificates in November 2014.
Microsoft and Mozilla will begin phasing out trust for SHA-1 certificates in 2016. With these dates fast approaching, it’s time to move to SHA-2.
- November 2014 – SHA-1 SSL Certificates expiring any time in 2017 will show a warning in Chrome.
- December 2014 – SHA-1 SSL Certificates expiring after June 1, 2016 will show a warning in Chrome
- January 2015 – SHA-1 SSL Certificates expiring any time in 2016 will show a warning in Chrome.
- January 1, 2016 – Microsoft will end trust for SHA-1 Code Signing Certificates without time stamps.
- January 1, 2017 – Microsoft and Mozilla will end trust for all SHA-1 SSL Certificates.
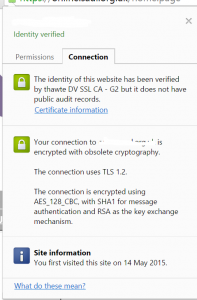
This screenshot shows a public website certificate warning in Chrome. The site uses TLS1.2 which is fine but the certificate hash is SHA-1:
Generating a CSR for a SHA-2 certificate:
openssl req -new -newkey rsa:2048 -nodes -sha256 -out www.mydomain.com.sha256.csr -keyout www.mydomain.key
At the time of writing, if you wish to generate a SHA-2 CSR for a certificate on an F5 Load Balancer, you will be unable to do it via the web UI but you can use openssl from the bash shell. You can then import the private key via the web interface, and send the CSR to the CA to get your certificate.
OLDER CLIENTS
Many older clients don’t support SHA256, but the real question is which of those are relevant? The answer will vary depending on the site. For detailed information on client capabilities, head to GlobalSign, which maintains a detailed summary of SHA256 support for a large number of platforms.
On the desktop, Windows XP introduced SHA256 in Service Pack 3. Users running SP2 should be able to upgrade to SP3. Depending on a site’s profile, a significant chunk of the user base might be running XP. This operating system is still very popular in China and there is also strong anecdotal evidence that it remains widely used in some large organizations.
Among the mobile platforms, Android added SHA256 support in version 2.3. Earlier versions—still used in large numbers—support only SHA1.