TCP Options and Riverbed WAN Acceleration Appliances
Normal TCP options are Type 0 (End of Option List), 1 (No-Operation), 2 (Maximum Segment Size, len 4), 3 (WSOPT – Window Scale, len 3), 4 (SACK Permitted, len 2), 5 (SACK, len N), and 8 (TSOPT – Time Stamp Option, len 10).
Maximum Segment Size (MSS): This is used to exchange Maximum Transfer Unit (MTU) and Maximum Receive Unit (MRU) sizes during the TCP three-way handshake. Meaning that both ends of the connection will state the maximum IP datagram size that they can handle without using fragmentation. The lower of the two values will be used by both ends.
No operation (NOP) : Used to provide padding around other options. The length of the TCP header must be a multiple of 4 bytes; however, most of the options are not 4 bytes long. If the total length of the options is not a 4-byte multiple, one or more 1-byte NOPs will be added to the options in order to adjust the overall length.
Window Scale (WSCALE) : Used to increase the window size from a 16 bit value to a 32 bit one. used to record how many bytes of buffer space the host has available for receiving data. Because the window size field is only 16 bits long, this limits the maximum window size to 65,535 bytes. You should only ever see this option though during the three way TCP/IP handshake.
Selective Acknowledgments: (there are two TCP options for selective acknowledgments):
- Selective Acknowledgment Permitted (SackOK): This option simply says that selective acknowledgments are permitted for this connection. SackOK must be included in the TCP options in both the SYN and SYN/ACK packets during the TCP three-way handshake, or it cannot be used. SackOK should not appear in any other packets.
- Selective Acknowledgment Data: This option contains the actual acknowledgment information for a selective acknowledgment. It lists one or more pairs of sequence numbers, which define ranges of packets that are being acknowledged.
Timestamp : There are two uses for this option as used by TCP. One is to calculate the RTT or return trip time and the second is used to prevent the PAWS aka protect against wrapped sequences, attack. This is an option which can be seen in a packet.
Record Route : This IP option has a kind value of seven and is of a variable length. This record route is used in conjunction with the other two IP options of “Loose Source route” and “Strict source route”. Their kind values are respectively 131 and 137. Record route or more specifically Loose Source Record Route packets have been a longstanding computer security concern. Back in 2002 I was able to determine that W2K and XP were still reversing the first hop of a LSRR packet. This was allowed by default on those TCP/IP stacks.
Riverbed TCP Option 76 and 78 :
Riverbed uses Option Type 76 and 77 (depending upon the “WAN Visibility”, or transparency mode used). You can see these using the CLI comand:
Steelhead # show sport kernel probe-tcp-opt
Probe TCP option: 76
Steelhead # show sport kernel trpy-tcp-opt
Transparency TCP option: 78
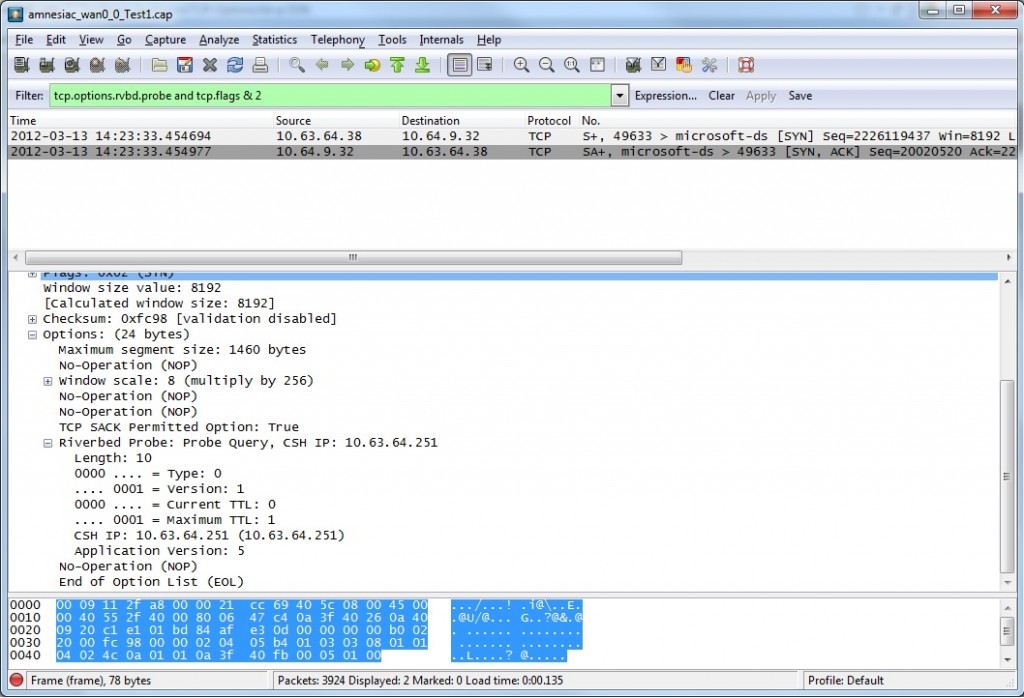
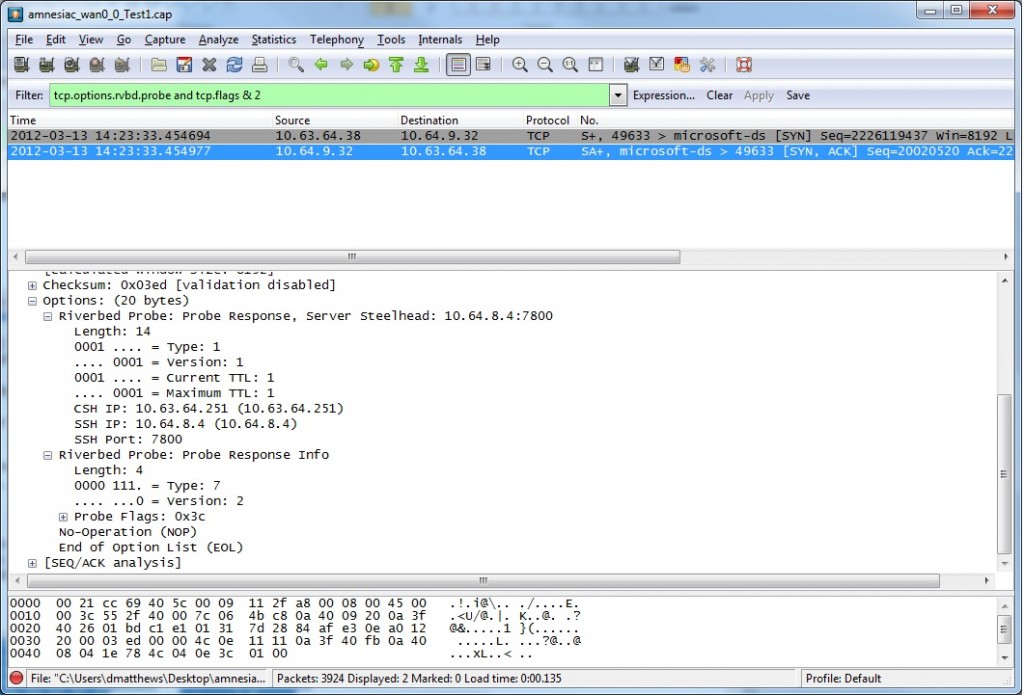
In a packet capture, you can apply a Wireshark filter to view the contents of a Probe Request and Response by using the filter: “tcp.options.rvbd.probe and tcp.flags & 2“
The probe request and response contains the IP address and service port used by the peer Steelhead Appliances:
Other Riverbed-Specific Wireshark Filters:
| tcp.options.rvbd.probe | Boolean | Riverbed Probe | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.appli_ver | Unsigned integer, 2 bytes | Application Version | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.client.ip | IPv4 address | Client IP | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.flags | Unsigned integer, 1 byte | Probe Flags | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.flags.last | Boolean | Last Notify | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.flags.notcfe | Boolean | Not Client-Side Steelhead | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.flags.probe | Boolean | Disable Probe Cache on Client-Side Steelhead | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.flags.server | Boolean | Server-Side Steelhead outer channel (optimised connection) to server established | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.flags.ssl | Boolean | SSL (Secure Sockets Layer) Enabled | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.len | Unsigned integer, 1 byte | Length | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.prober | IPv4 address | Client-Side Steelhead IP Address | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.proxy.ip | IPv4 address | Server-Side Steelhead IP Address | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.proxy.port | Unsigned integer, 2 bytes | Server-Side Steelhead Port | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.storeid | Unsigned integer, 4 bytes | Client-Side Steelhead Store ID | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.type1 | Unsigned integer, 1 byte | Type | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.type2 | Unsigned integer, 1 byte | Type | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.version | Unsigned integer, 1 byte | Version | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.probe.version_raw | Unsigned integer, 1 byte | Version | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy | Boolean | Riverbed Transparency | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.client.port | Unsigned integer, 2 bytes | Out of band connection Client Port | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.dst.ip | IPv4 address | Dst SH IP Addr | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.dst.port | Unsigned integer, 2 bytes | Dst SH Inner Port | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.flags | Unsigned integer, 2 bytes | Transparency Options | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.flags.chksum | Boolean | Reserved | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.flags.fw_rst | Boolean | Enable Transparency FW feature on All FWs | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.flags.fw_rst_inner | Boolean | Enable Inner FW feature on All FWs | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.flags.fw_rst_probe | Boolean | Enable FW traversal feature | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.flags.mode | Boolean | Transparency Mode | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.flags.oob | Boolean | Out of band connection | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.src.ip | IPv4 address | Src SH IP Addr | 1.6.0 to 1.6.5 |
| tcp.options.rvbd.trpy.src.port | Unsigned integer, 2 bytes | Src SH Inner Port | 1.6.0 to 1.6.5 |
sources: self-testing / riverbed / symantec / wireshark wiki