SSL/TLS Handshake and Record Data Protocol
When an TLS/SSL session (such as HTTPS (default port 443) is established an SSL handshake or exchange of messages occur between the client (initiating the connection) – and a server. (See this post for an explanation of SSL certificates and encoding).
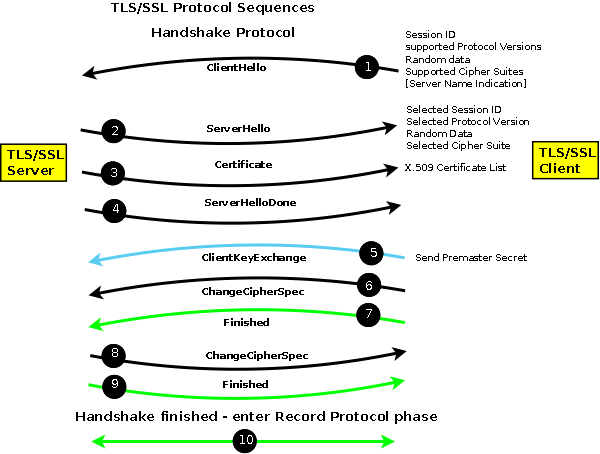
The first set of messages are called the Handshake Protocol after which both client and server enter the Record (or Data) Protocol. The messages exchanged during the Handshake Protocol achieves the following:
- Establishes the protocol version and variant to be used from the supported set of SSLv3, TLSv1, TLSv1.1, TLSv1.2. The latest possible variant will always be used (for example TLSv1 would always preferred to SSLv3 if both client and server support both types. The client offers a list and the server makes the choice from the offered list.
- Sends authentication data. The server sends authentication information usually wrapped in an X.509 (SSL) certificate. (Other methods are supported by the protocol.
- Establishes a session ID so that the session can be restarted if required.
- Negotiates a Cipher Suite consisting of a key-exchange algorithm together with a bulk-data encryption algorithm type and a MAC type used in the subsequent data session (Record Protocol). The key-exchange algorithm typically uses an asymmetric (public-private key) algorithm such as RSA, DSA or ECC (Elliptic Curve Cipher – see RFC5289). Asymmetric algorithms are very expensive in resources (CPU) and therefore symmetric ciphers are used for subsequent bulk-data encryption (using the Record Protocol). The key-exchange algorithm is used to transfer information from which session key(s) can be independently computed for the symmetric (bulk-data) cipher. The MAC protects the integrity of the transmitted/received data during the Record Protocol.
This a simplified overview and additional data may be exchanged, for instance, the client can be requested to send an authenticating X.509 (SSL) certificate in a process called mutual authentication, but the above describes the most common case and is illustrated in the figure below:
PLEASE NOTE:
The Handshake Protocol negotiates and establishes the connection and the Record Protocol transfers (encapsulates) the encrypted data stream such as HTTP, SMTP or IMAP.
In the figure above, messages in black are sent in clear, messages in blue are sent using the public key supplied by the server (using the key-exchange cipher), messages in green are sent using the negotiated bulk-data cipher and are protected by the negotiated MAC.
TLS/SSL allows for a data compression algorithm to be negotiated as part of the cipher suite. Given the speed of modern networks data compression is rarely, if ever, used and is typically set to the value NULL (not used).