An NTP server can provide synchronised date and times for devices in a network. Since a router cannot be a Stratum 1 device (cannot connect to a Stratum 0 device such as a GPS clock), a router is not an accurate source of time information. If this is not important to you, then using a router as an NTP server may be acceptable. Read more…
If nslookup fails on CentOS, you may need to install bind utilities: Read more…
SIGTERM vs. SIGKILL
Sending signals to processes using kill on a Unix system is not a new topic for most systems administrators, but I’ve been asked many times about the difference between kill and kill -9. Read more…
Moving your applications into “the cloud” means that round-trip times and protocol and application latency can become a serious issue.
The Riverbed Virtual Steelhead Appliance, a software version of Riverbed Technology’s WDS solution is worth considering:
Read more…
Bob Gilbert discusses how Riverbed Technology RSP provides “one-box” solution for local delivery of virtualized industry-standard applications, speeding up your network:
Read more…
When multiple WAEs exist in a service group, WCCPv2 automatically distributes redirected traffic across all WAEs in the service group. When traffic passes through an IOS device with WCCPv2 redirection configured, the IOS device assigns traffic for that connection to a bucket. Read more…
The routers and WAEs participating in the same service constitute a service group. A service group defines a set of characteristics about what types of traffic should be intercepted, as well as how the intercepted traffic should be handled. There are two types of service groups:
- Well-known services
- Dynamic services
Well-known services, also referred to as static services, have a fixed set of characteristics that are known by both IOS and WCCPv2 client devices. Read more…
ngrep is a “network grep” utility that can be used to match regular expressions within network packet payloads. This is a very handy utility as many network analysers (“packet sniffers”) can examine the packet header, but either do not display or cannot filter based on packet payload. Read more…
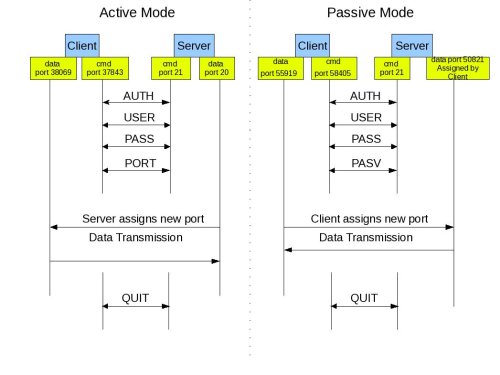
Active FTP:
In active mode FTP the client connects from a random unprivileged port (N > 1023) to the FTP server’s command port, port 21. Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server. The server will then connect back to the client’s specified data port from its local data port, which is port 20.
From the server-side firewall’s standpoint, to support active mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s port 20 to ports > 1023 (Server initiates data connection to client’s data port)
* FTP server’s port 20 from ports > 1023 (Client sends ACKs to server’s data port)
Passive FTP:
In order to resolve the issue of the server initiating the connection to the client a different method for FTP connections was developed. This was known as passive mode, or PASV, after the command used by the client to tell the server it is in passive mode.
In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server. When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1023 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command. The result of this is that the server then opens a random unprivileged port (P > 1023) and sends the PORT P command back to the client. The client then initiates the connection from port N+1 to port P on the server to transfer data.
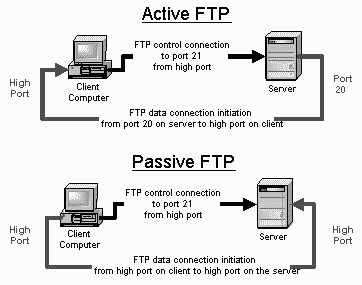
From the server-side firewall’s standpoint, to support passive mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s ports > 1023 from anywhere (Client initiates data connection to random port specified by server)
* FTP server’s ports > 1023 to remote ports > 1023 (Server sends ACKs (and data) to client’s data port)
Introduction
Riverbed Steelhead as WAN accelerator is deployed in WAN environment when traffic between WAN network (i.e. MPLS, Frame Relay) need to be optimized, hence creating so-called “WAN acceleration”. With “standard” WAN network consists of WAN routers and LAN switches, typically the Riverbed Steelhead is in place inline between the WAN routers and LAN switches. The f9llowing is an illustration: Read more…


