At its core an X.509 certificate is a digital document that has been encoded and/or digitally signed according to RFC 5280.
In fact, the term X.509 certificate usually refers to the IETF’s PKIX Certificate and CRL Profile of the X.509 v3 certificate standard, as specified in RFC 5280, commonly referred to as PKIX for Public Key Infrastructure (X.509). (See this post for an explanation of the SSL/TLS Handshake and Record Protocols). Read more…
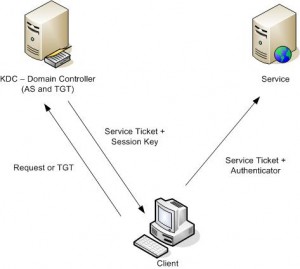 The Kerberos authentication method originated at the Massachusetts Institute of Technology in the 1980s.
The Kerberos authentication method originated at the Massachusetts Institute of Technology in the 1980s.
It was part of a project called Athena that involved integrating the computers on the MIT campus, which ran on different operating systems, in a network that offered single sign-on (SSO).
At that time, most UNIX systems allowed users to access their resources as long as they had an account name and password. Read more…
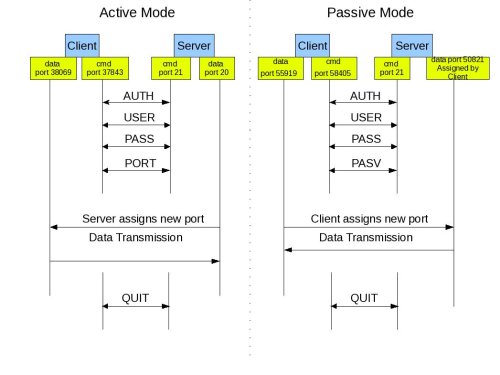
Active FTP:
In active mode FTP the client connects from a random unprivileged port (N > 1023) to the FTP server’s command port, port 21. Then, the client starts listening to port N+1 and sends the FTP command PORT N+1 to the FTP server. The server will then connect back to the client’s specified data port from its local data port, which is port 20.
From the server-side firewall’s standpoint, to support active mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s port 20 to ports > 1023 (Server initiates data connection to client’s data port)
* FTP server’s port 20 from ports > 1023 (Client sends ACKs to server’s data port)
Passive FTP:
In order to resolve the issue of the server initiating the connection to the client a different method for FTP connections was developed. This was known as passive mode, or PASV, after the command used by the client to tell the server it is in passive mode.
In passive mode FTP the client initiates both connections to the server, solving the problem of firewalls filtering the incoming data port connection to the client from the server. When opening an FTP connection, the client opens two random unprivileged ports locally (N > 1023 and N+1). The first port contacts the server on port 21, but instead of then issuing a PORT command and allowing the server to connect back to its data port, the client will issue the PASV command. The result of this is that the server then opens a random unprivileged port (P > 1023) and sends the PORT P command back to the client. The client then initiates the connection from port N+1 to port P on the server to transfer data.
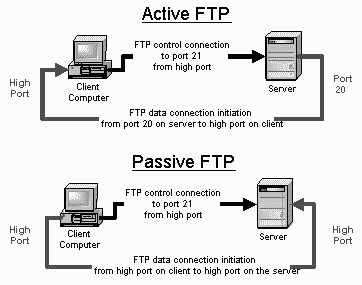
From the server-side firewall’s standpoint, to support passive mode FTP the following communication channels need to be opened:
* FTP server’s port 21 from anywhere (Client initiates connection)
* FTP server’s port 21 to ports > 1023 (Server responds to client’s control port)
* FTP server’s ports > 1023 from anywhere (Client initiates data connection to random port specified by server)
* FTP server’s ports > 1023 to remote ports > 1023 (Server sends ACKs (and data) to client’s data port)
How to set up an IPSec tunnel between two LANs using the same subnet.
Conflicting LAN IP subnets can cause difficulties when routing through a tunnel. This configuration uses NAT to overcome the problem of duplicate addresses: Read more…
TCP and UDP small servers are servers (daemons, in Unix parlance) that run in the router which are useful for diagnostics. Read more…
Context-Based Access Control (CBAC) intelligently filters TCP and UDP packets based on application layer protocol session information and can be used for intranets, extranets and internets. CBAC can be configured to permit specified TCP and UDP traffic through a firewall only when the connection is initiated from within the network needing protection.
CBAC can inspect traffic for sessions that originate from either side of the firewall. This is the basic function of a stateful inspection firewall. Read more…
A base Access List for any internet facing router, re-produced from Mike Storm and Jeremy Cioara’s blogs:
Read more…
This quick lab demonstrates how CBAC is configured and applied to interfaces.
Read more…
Try this quick and simple practice lab, where a secure IPsec tunnel is configured between two routers. Use debug to see ISAKMP and IPsec working.
Read more…



