
HTTP and ETag
Download this capture file: ” IfModifieldSince_and_ETag ”
OR: view it now via Cloudshark
With caching enabled, a web server does not need to send a full response if content has not changed.
- If-Modified-Since is an HTTP request header that the client sends to your browser along with a request for content.
- Last-Modified is an HTTP response header that the server returns along with the requested content.
If-Modified-Since Allows a 304 Not Modified to be returned if content is unchanged
If-Modified-Since: Sat, 29 Oct 1994 19:43:31 GMT
If-None-Match Allows a 304 Not Modified to be returned if content is unchanged,
If-None-Match: "737060cd8c082f209582d" Read more…

WCCP
Refer to this Wireshark Capture. OR: view it now via Cloudshark
Alternatively, Download: WCCPv2.pcap and continue reading.. Read more…
The TCPDUMP filter to match a DSCP is a little tricky to construct. I need to explain how the filter works and also what TCPDUMP sees in the ToS Byte of the IP header and then how to filter on just the DiffServ extensions.
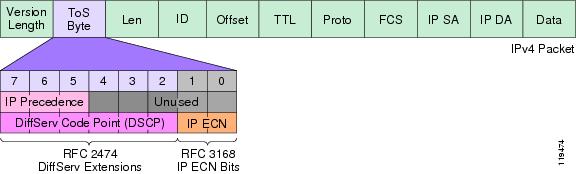
The IP ToS Byte (DSCP and IP ECN)
FIRST THE ANSWER:
(in case it is not important to understand how the filter is constructed)
– an example filtering on DSCP decimal 20 (AF22):
tcpdump -i eth0 (ip and (ip[1] & 0xfc) >> 2 == 20) -vvv
– An example filtering on DSCP Hex 14 (also decimal 20 or AF22):
tcpdump -i eth0 (ip and (ip[1] & 0xfc) >> 2 == 0x14) –vvv
Read more…
This post describes typical message exchange sequence for a client connecting to a user level server, opening a file, reading its data, closing the file, and disconnecting from the server. Opportunistic Locking (Oplocks) are also explained.
You can also refer tothis capture: Download smbtorture from Wireshark Wiki to further understand the SMB dialogues. The capture was made using the Samba4 smbtorture suite, against a Windows Vista beta2 server. Read more…
When a client connects to a server using SMB it sends a “Negotiate Protocol Request”. In response to this, the server replies with a “Negotiate Protocol Response”. This response reveals whether SMB signing is enabled and whether it is required at the client, the server, or both. Read more…
Normal TCP options are Type 0 (End of Option List), 1 (No-Operation), 2 (Maximum Segment Size, len 4), 3 (WSOPT – Window Scale, len 3), 4 (SACK Permitted, len 2), 5 (SACK, len N), and 8 (TSOPT – Time Stamp Option, len 10). Read more…
IEEE 802.11n uses the multiple-input-multiple-output (MIMO) technology that enables spatial signal diversity and spatial signal multiplexing enabling increased range and data transmission rates. 802.11n allows use of wider 40 MHz channels to double the bandwidth as compared to the legacy 20 MHz operation.
AirPcap NX adaptors can be configured to capture data on 40MHz channels but you will need to determine the “extension channel” Read more…

