Xen Hypervisor
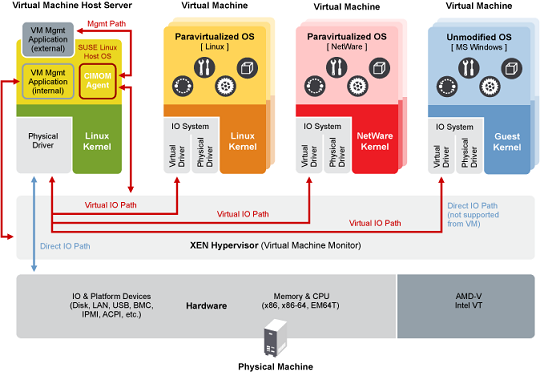
The Open Source Xen hypervisor runs directly on the hardware and becomes the interface for all hardware requests such as CPU, I/O, and disk for the guest operating systems. By separating the guests from the hardware, the Xen hypervisor is able to run multiple operating systems securely and independently.
The Domain 0 Guest referred to as Dom0 is launched by the Xen hypervisor during initial system start-up and can run any operating system except Windows. The Dom0 has unique privileges to access the Xen hypervisor that is not allocated to any other Domain Guests. These privileges allow it to manage all aspects of Domain Guests such as starting, stopping, I/O requests, etc. A system administrator can log into Dom0 and manage the entire computer system.
The Domain Guests referred to as DomUs or unprivileged domains are launched and controlled by the Dom0 and independently operate on the system. These guests are either run with a special modified operating system referred to as paravirtualizion or un-modified operating systems leveraging special virtualization hardware (Intel VT and AMD-V) referred to as hardware virtual machine (HVM). Note: Microsoft Windows requires a HVM Guest environment.
Paravirtualization
A term used to describe a virtualization technique that allows the operating system to be aware that it is running on a hypervisor instead of base hardware. The operating system must be modified to accommodate the unique situation of running on a hypervisor instead of basic hardware.
Hardware Virtual Machine (HVM)
A term used to describe an operating system that is running in a virtualized environment unchanged and unaware that it is not running directly on the hardware. Special hardware is required to allow this, thus the term HVM.
such as CPU, I/O, and disk for the guest operating systems. By separating the guests from the
hardware, the Xen hypervisor is able to run multiple operating systems securely and independently.
The Domain 0 Guest referred to as Dom0 is launched by the Xen hypervisor during initial system
start-up and can run any operating system except Windows. The Dom0 has unique privileges to access
the Xen hypervisor that is not allocated to any other Domain Guests. These privileges allow it to
manage all aspects of Domain Guests such as starting, stopping, I/O requests, etc. A system
administrator can log into Dom0 and manage the entire computer system.
The Domain Guests referred to as DomUs or unprivileged domains are launched and controlled by the
Dom0 and independently operate on the system. These guests are either run with a special modified
operating system referred to as paravirtualizion or un-modified operating systems leveraging special
virtualization hardware (Intel VT and AMD-V) referred to as hardware virtual machine (HVM). Note
– Microsoft Windows requires a HVM Guest environment.
• Paravirtualization
A term used to describe a virtualization technique that allows the operating system to be aware
that it is running on a hypervisor instead of base hardware. The operating system must be
modified to accommodate the unique situation of running on a hypervisor instead of basic
hardware.
• Hardware Virtual Machine (HVM)
A term used to describe an operating system that is running in a virtualized environment
unchanged and unaware that it is not running directly on the hardware. Special hardware is
required to allow this, thus the term HVM.
With Xen virtualization, a thin software layer known as the Xen hypervisor is inserted between the server’s hardware and the operating system. This provides an abstraction layer that allows each physical server to run one or more “virtual servers”, effectively decoupling the operating system and its applications from the underlying physical server.
The Xen hypervisor is a unique open source technology, developed collaboratively by the Xen community and engineers at over 50 of the most innovative data center solution vendors, including AMD, Cisco, Dell, Fujistu, HP, IBM, Intel, Mellanox, Network Appliance, Novell, Red Hat, Samsung, SGI, Sun, Unisys, Veritas, Voltaire, and Citrix. Xen is licensed under the GNU General Public License (GPL2) and is available at no charge in both source and object format. Xen is, and always will be, open sourced, uniting the industry and the Xen ecosystem to speed the adoption of virtualization in the enterprise.
The Xen hypervisor is also exceptionally lean– less than 150,000 lines of code. That translates to extremely low overhead and near-native performance for guests. Xen re-uses existing device drivers (both closed and open source) from Linux, making device management easy. Moreover Xen is robust to device driver failure and protects both guests and the hypervisor from faulty or malicious drivers.
Source of information: http://www.xen.org
Visit the Xen community at: http://www.xen.org/community/
LinkedIn: Xen Masters