DNS – IN-ADDR.ARPA Reverse Mapping
IPv4 IN-ADDR.ARPA Reverse Mapping Domain
We defined the normal domain name structure as a tree starting from the root. We write a normal domain name LEFT to RIGHT but the hierarchical structure is RIGHT to LEFT.
domain name = www.example.com
highest node in tree is = .com
next (lower) = .example
next (lower) = www
An IPv4 address is written as:
192.168.23.17
This IPv4 address defines a host (17) which happens to be in a Class C address range (192.168.23.x). In this case the most important part (the highest node) is on the LEFT (192) not the RIGHT. This is a tad awkward and would make it impossible to construct a sensible tree structure that could be searched in a single lifetime.
The solution is to reverse the order of the address and place the result under the special domain IN-ADDR.ARPA (you will see this also written as in-addr.arpa which is perfectly legitimate since domain names are case insensitive but the case should be preserved between query and response, so we will continue to use IN-ADDR.ARPA. You may elect to use whatever you wish including IN-addr.Arpa if that is your preference).
Finally the last part of the IPv4 Address (17) is the host address and hosts, from our previous reading, are typically defined inside a zone file so we will ignore it and only use the Class C address base. The result of our manipulations are:
IP address =192.168.23.17
Class C base = 192.168.23 ; omits the host address = 17
Reversed Class C base = 23.168.192
Added to IN-ADDR.ARPA domain = 23.168.192.IN-ADDR.ARPA
This is show in the figure here:
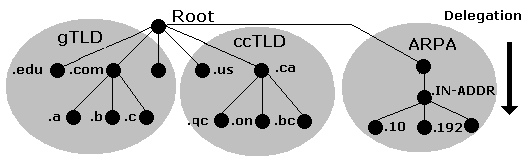
arpa organization
IN-ADDR.ARPA Reverse Mapping
Finally we construct a zone file to describe all the hosts (nodes) in the Reverse Mapped zone using PTR Records ( see this post for more about PTR records ). The resulting file will look something like this:
$TTL 2d ; 172800 seconds
$ORIGIN 23.168.192.IN-ADDR.ARPA.
@ IN SOA ns1.example.com. hostmaster.example.com. (
2003080800 ; serial number
3h ; refresh
15m ; update retry
3w ; expiry
3h ; nx = nxdomain ttl
)
IN NS ns1.example.com.
IN NS ns2.example.com.
1 IN PTR www.example.com. ; qualified name
2 IN PTR joe.example.com.
.....
17 IN PTR bill.example.com.
.....
74 IN PTR fred.example.com.
....
We must use qualified names ending with a dot (in fact they are Fully Qualified Domain Names – FQDNs) in reverse mapped zone files because if we did not our $ORIGIN directive would lead to some strange results. For example, if we wrote an unqualified name such as:
74 IN PTR fred
Using the $ORIGIN substitution rule the above would expand to fred.23.168.192.IN-ADDR.ARPA. which is probably not what we intended.
