NetFlow Primer
Because it is part of Cisco IOS software, NetFlow enables networks to perform IP traffic flow analysis without deploying external probes, making traffic analysis economical even on large IP networks.
The key components of NetFlow are the NetFlow cache that stores IP flow information and the NetFlow export mechanism that sends NetFlow data to a collector, such as the NetFlow Collector. These two key components, the metering process and the exporting process, sometimes lead to confusion, because the term “NetFlow” refers to both of them.
NetFlow operates by creating a NetFlow cache entry (also called flow record) for each active flow
NetFlow maintains a flow record within the cache for active flows. Each flow record contains multiple data fields, which are exported to a NetFlow collector. The Cisco NetFlow Collection Engine (NFC) is a device that provides flow filtering and aggregation capabilities. Afterwards, Network Management applications, such as performance monitoring, security analysis, and billing solutions, can access the aggregated NetFlow records for further processing.
NetFlow does not involve any connection-setup protocol between routers, networking devices, or end stations. NetFlow does not change the IP packets and is transparent to the existing network infrastructure.
A flow is defined as a set of packets having common properties: one or more packet header fields (e.g. destination IP address, transport header field), one or more characteristics of the packet itself .
A packet belongs to a flow record if it completely matches all defined flow properties.
NetFlow defines a flow by a combination of key-fields in the packet, called “flow keys”. Usually additional information is reported in a flow, such as number of packets and bytes, start and stop time, and so on. These reporting fields do not define a flow; therefore, they are called “flow values” or “non-key-fields”.
Initially, NetFlow defines a flow as the combination of the following seven key-fields:
- Source IP address.
- Destination IP address.
- Source port number.
- Destination port number.
- Layer 3 protocol type.
- ToS byte.
- Logical interface (ifIndex), which is the input ifIndex in case of ingress NetFlow, or the output ifIndex with egress NetFlow. (Note also that the command ip flow-egress input-interface lets you use the input ifIndex as a key-field even if NetFlow egress is configured. This means that the input ifIndex is an additional key-field).
Specific to the router, the “router-based aggregation feature” aggregates the flow records further. It works by reducing or modifying the initial set of seven key-fields.
For example, as described in Table 1-1, the Protocol Port-TOS aggregation type applies the source and destination application ports as key-fields. Alternatively, the destination IP address key-field can be modified to the destination prefix key-field, entailing flow records aggregation.
|
Table1-1 ToS-Based Aggregation Schemes |
||||||
|
|
AS-TOS |
Protocol Port-TOS |
Source Prefix-TOS |
Destination Prefix-TOS |
Prefix-TOS |
Prefix-Port |
|
Source Prefix |
|
|
X |
|
X |
X |
|
Source Prefix Mask |
|
|
X |
|
X |
X |
|
Destination Prefix |
|
|
|
X |
X |
X |
|
Destination Prefix Mask |
|
|
|
X |
X |
X |
|
Source Application Port |
|
X |
|
|
|
X |
|
Destination Application Port |
|
X |
|
|
|
X |
|
Input Interface |
X |
X |
X |
|
X |
X |
|
Output Interface |
X |
X |
|
X |
X |
X |
|
IP Protocol |
|
X |
|
|
|
X |
|
Source AS |
X |
|
|
|
|
|
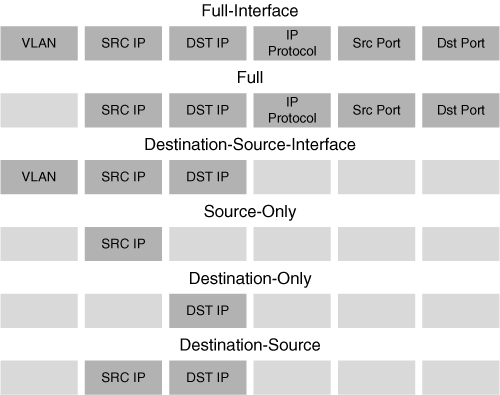
Additionally, the Catalyst 6500/Cisco 7600 offers extra flexibility in the key-field configuration. The flow mask is used for data aggregation in the NetFlow cache. You can select (configure) the flow mask from a predefined set of values. For example, if you are interested in the traffic accounting per source and destination IP address, the destination-source (see Figure 7-2) is the best flow mask option, because it uses only the source and destination IP addresses as key-fields to classify the observed packets.
This “flow mask” concept is different from the router-based aggregation scheme. Router-based aggregation uses multiple caches; data aggregation is performed by processing flow entries as they expire from the main cache. Flow mask aggregates the flow information directly into the main NetFlow cache on the Catalyst 6000/Cisco 7600.
The characteristics of active flows can be analyzed by displaying the cache, which makes NetFlow a powerful troubleshooting tool, even without exporting the flow records to a collector. For a better understanding, look at the following output from the NetFlow command show ip cache flow:
7200-netflow#show ip cache flow
1. IP packet size distribution (1693 total packets):
2. 1-32 64 96 128 160 192 224 256 288 320 352 384 416 448 480
3. .000 .190 .190 .615 .000 .000 .000 .000 .000 .000 .000 .000 .000 .000
.000
4. 512 544 576 1024 1536 2048 2560 3072 3584 4096 4608
5. .000 .000 .003 .000 .000 .000 .000 .000 .000 .000 .000
6. IP Flow Switching Cache, 4456704 bytes
7. 2 active, 65534 inactive, 7 added
8. 120 ager polls, 0 flow alloc failures
9. Active flows timeout in 30 minutes
10. Inactive flows timeout in 15 seconds
11. last clearing of statistics 00:03:18
12. Protocol Total Flows Packets Bytes Packets Active (Sec) Idle (Sec)
13. ----- Flows /Sec /Flow /Pkt /Sec /Flow /Flow
14. TCP-Telnet 3 0.0 12 106 0.1 4.2 15.8
15. ICMP 2 0.0 500 100 5.2 2.6 15.4
16. Total: 5 0.0 207 100 5.4 3.6 15.6
17. SrcIf SrcIPaddress DstIf DstIPaddress Pr SrcP DstP Pkts
18. Et0/0 10.10.10.34 Et0/0 10.10.10.255 11 0208 0208 1
19. Se3/0.16 10.1.10.1 Fa4/0 192.168.10.1 06 0017 2AFF 6
The first portion of the output, in lines 1 through 5, is the packet size distribution. Several questions that operators ask are answered here, such as “What percentage of packets of each size have passed through this router?” This information can be very useful for network troubleshooting, traffic engineering, and capacity planning.
Lines 6 through 8 describe the parameters assigned to the NetFlow cache. The default maximum number of cached flows is 65,536. In this example, two cache entries are in use, and 65,534 are available for new flows. Furthermore, the “added” parameter on line 7 displays the total number of flows examined in the cache.
Lines 9 through 11 show how long a particular flow will stay in the cache. In this example, if there were no activity on the flow for 15 seconds, the entry would have been exported and purged from the cache. If an active entry is in the cache for 30 minutes, it is expired, even if traffic still exists. A new cache entry is built on the receipt of the next packet for that particular flow. Connection-oriented flows, such as Telnet and FTP, are purged as soon as the session is closed, which is identified by TCP-FIN (finish) or TCP-RST (reset) packets.
Lines 12 through 16 break down the flows by protocol. Again, this is an ideal source of information for the network administrator, because it lists traffic distribution by type of applications.
Lines 17 through 19 show the actual NetFlow cache entries.
———————————————————————————————–
Post courtesy:
http://etutorials.org
|
Table 7-3. ToS-Based Aggregation Schemes |
||||||
|
|
AS-TOS |
Protocol Port-TOS |
Source Prefix-TOS |
Destination Prefix-TOS |
Prefix-TOS |
Prefix-Port |
|
Source Prefix |
|
|
|
|
|
|
|
Source Prefix Mask |
|
|
|
|
|
|
|
Destination Prefix |
|
|
|
|
|
|
|
Destination Prefix Mask |
|
|
|
|
|
|
|
Source Application Port |
|
|
|
|
|
|
|
Destination Application Port |
|
|
|
|
|
|
|
Input Interface |
|
|
|
|
|
|
|
Output Interface |
|
|
|
|
|
|
|
IP Protocol |
|
|
|
|
|
|
|
Source AS |
|
|
|
|
|
|